Web Application Firewall | WAF
Arvancloud WAF uses Regex rules and blocks malicious requests based on the Anomaly Scoring method. The method recognizes threats with high accuracy where every rule is assigned a value. The accumulation of the values for every received request is calculated to determine whether it goes beyond the defined WAF threshold. The request is blocked when the computed value is the same or higher than the specified threshold.
This page explains the settings and configuration of Arvancloud’s WAF.
Settings and Configuration of Arvancloud’s WAF
To change WAF settings, go to your Arvancloud user panel in the CDN section and click on WAF.
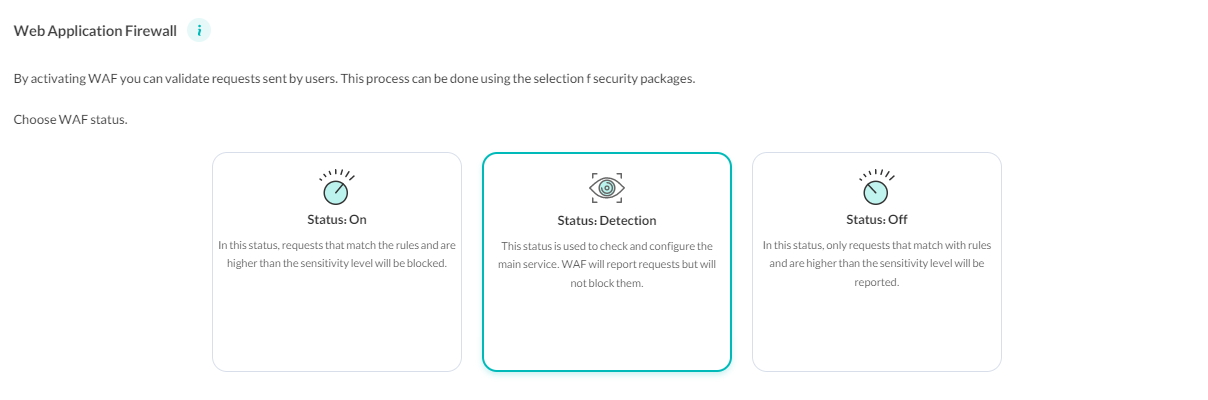
In WAF general setting, you can set your WAF settings to one of the presented ones in the Web Application Firewall section.
-
Turning the status off, WAF will be disabled on your website.
Turning WAF off using API:
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/waf' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data-raw '{"mode":"off"}'
When the setting is set to Detection, WAF only logs reports. Please note that no requests are blocked in this case.
Activating Detection mode through API:
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/waf' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data-raw '{"mode":"detect"}'
-
Activating WAF protects your website against suspicious requests.
Turning WAF on using API:
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/waf' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data-raw '{"mode":"protect"}'
Before activating your WAF, we recommend that you configure your settings to recognize possible threats to distinguish real threats for a limited time.
After this period go to the WAF Attacks Analysis to see details and error codes related to attacks.
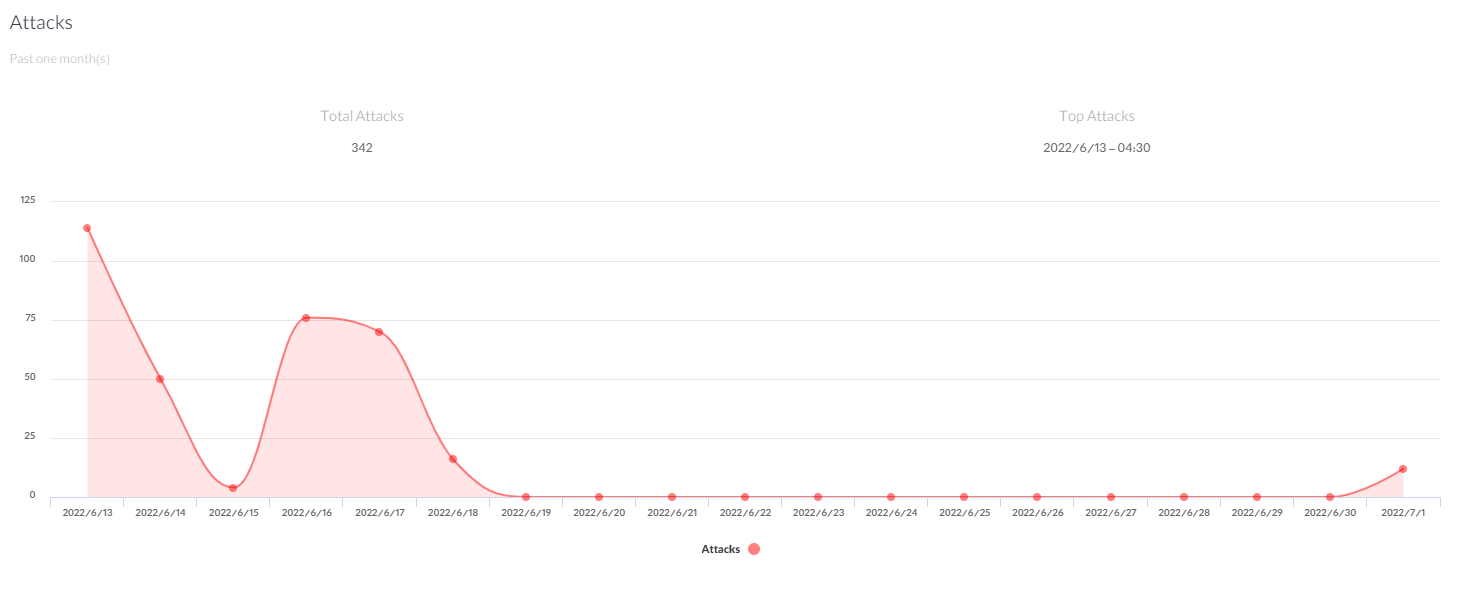
These logs help recognize False Positives, which means those requests that are not malicious but are recognized as such by WAF. False positives help in understanding which rules need to be deactivated. You can get the ID from the log and search it in the related security package to deactivate it. After this stage, you can activate your WAF and configure the Threshold and the rules according to your findings.
Disabling a specific rule with the API:
for this you need to send the "disabled_rules" parameter with the rules number.
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/waf/packages/default?revelio' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data-raw '{"disabled_rules":["21001","21003","21006","21009","40026","99001","21002"]}'
After the specified time for the WAF to be in detection mode, go to the WAF settings section, enable the "on" option and set the rules and specify the sensitivity according to what you got from the report section.
Note that when WAF is active, the maximum request Body size will be 524,288 bytes.
Higher sensitivity means more rules that need to be matched and lower WAF sensitivity. In other words, there is a reverse relationship between the number set for the sensitivity and WAF performance. Therefore, a lower number means higher WAF sensitivity.
Packages
By using security packages, you can add predefined settings to WAF depending on your needs. Each of the security packages has different settings that by activating the package, these settings are applied to your web firewall and are used in checking requests.

Currently, in addition to the default WAF package of Arvancloud, two standard packages CRS and Comodo can be activated and used from the packages section in the WAF user panel.
Arvancloud’s WAF Package
This package includes Arvancloud’s default WAF rules. The following section introduces and explains these rules.
-
Executing Malicious Codes XSS (Code 42xxx)
This attack is the result of executing the input (malicious code) by the browser without authentication. The attack can be sent through a URL in an email, loaded in the vulnerable parts of the website, or through other methods. The malicious script is then executed on users’ browsers to take control of their browsers.
-
SQL Injection Attacks (Code 41xxx)
In this attack, an unwanted SQL Query is sent from the user to the server through the input of a form or URL parameters. This attack makes it possible to read, create, edit and remove private information, change database data or create forbidden access for a specific user (such as taking away Admin’s accessibility).
-
Unusual Requests (Code 21xxx) The HTTP is attacked, and WAF evaluates the authenticity of HTTP headers by analyzing things such as the validity of the header, the presence of a valid value in the header, etc. in order to distinguish the authentic and malicious HTTP.
-
Malicious Bots (Code 35xxx) In this section, WAF blocks malicious bots. Normal bots all follow WAF rules and are not blocked in the process. However, bots that maliciously try to bypass WAF rules and seek to misuse the vulnerabilities in the applications are blocked by WAF.
-
Preventing Untypical HTTP Requests (Code 20xxx) In this state, WAF examines HTTP protocol performance to make sure that it works properly. Post/get methods are analyzed to check if they have bodies, or post request is examined to see whether the content length is present.
-
General Attacks (Code 40xxx) These attacks make use of the absence of authentication of input/output data to inject their malicious code into the program. Interpretation of the code can cause problems such as data can be stolen and the bypass of the authentication process. The most famous attacks are Remote File Inclusion (RFI) and Local File Inclusion (LFI).
CRS Package
This package includes the general rules for identifying attacks, and it can be used on Arvancloud’s CRM feature. You can protect your website against various attacks by activating WAF in your user panel and choosing the CRS package. This package also blocks the following common attacks.
SQL Injection (SQLi)
Cross Site Scripting (XSS)
Local File Inclusion (LFI)
Remote File Inclusion (RFI)
PHP Code Injection
Java Code Injection
HTTPoxy
Shellshock
Unix/Windows Shell Injection
Session Fixation
Scripting/Scanner/Bot Detection
Metadata/Error Leakages
Comodo Package
This package can be activated alongside other packages in the Arvancloud user panel. The package includes the main Rulesets of Intrusion Protection and Advanced Filtering.
Custom Rules
In Arvancloud Web Firewall, it is possible to enable or disable WAF protection for a specific path of the domain or an IP range. To do this, you must first go to the WAF section in the CDN panel, and then click on the "Add New Rule" in the "Custom Rules" section.

At this stage, you must enter the requested path in the form of Glob and the desired IP or IP range on which you decide to apply the rule. Finally, select the operation status.

After creating the rule, list of them will be displayed along with their priority, and on this page you can edit the rules. The priority specifies which rules will be executed first, and if there are multiple rules for a given path, which rule should be executed first.
Keep in mind that the lower the priority value of a rule, the sooner it will be executed. For example, a rule with priority 1 is considered before a rule with priority 10.
Create a custom rule with the API:
To specify the action of the rule, you must pass the "action" parameter with "protect" for protection or "passthrough" for no protection.
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/waf/rules' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'content-type: application/json' \
--data-raw '{"id":null,"url_pattern":"example.com/**","sources":["192.168.1.1/32"],"description":"Test For Docs","action":"protect"}'
WAF Attacks Analysis
You can read and analyze identified attacks in the Arvancloud WAF Attacks Analytics, where you can see the details of the attacks and change your rules according to the expected behavior of your website.
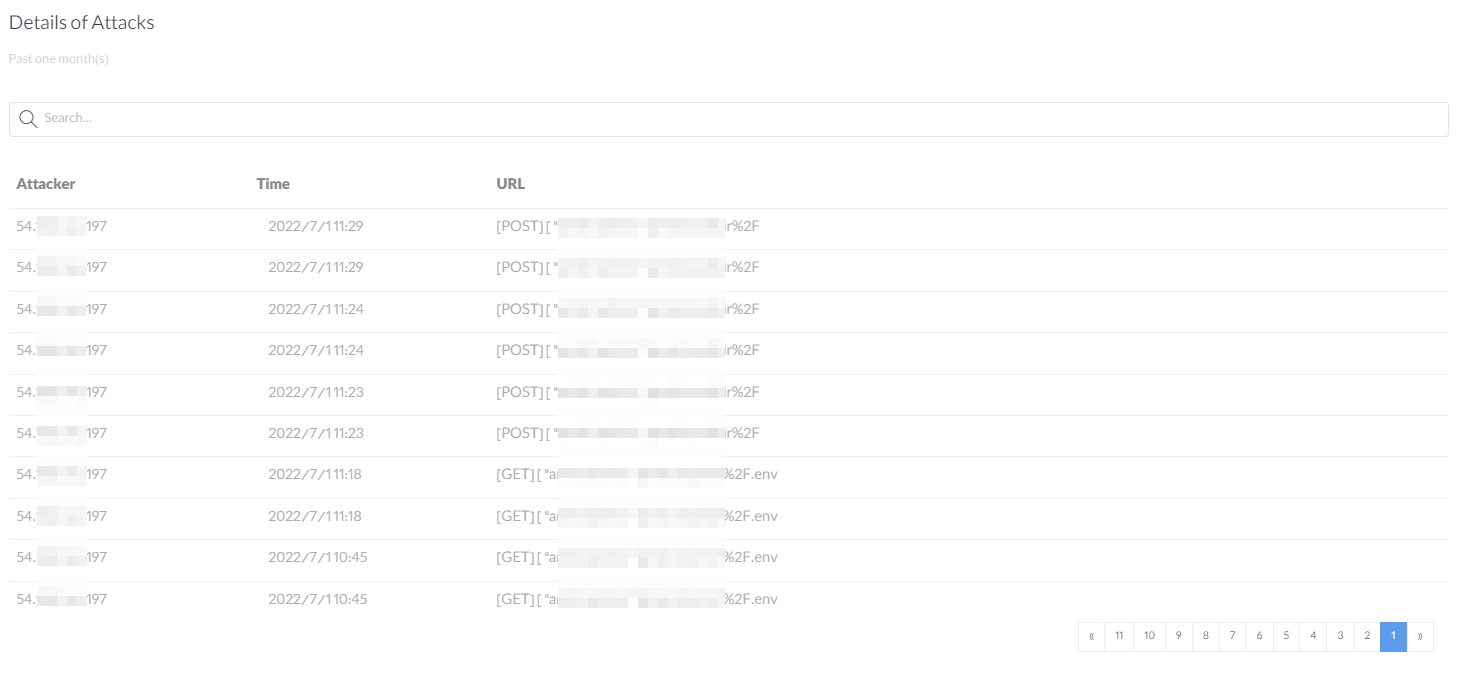
There is a log for every attack, and you can see this information in the given order:
- Attacker’s IP
- Request Method
- Attacked Address
- Time
- Sent Cookies
- User Agent
Then, you can see the rules that matched the request and note the ID if needed to deactivate it in WAF.
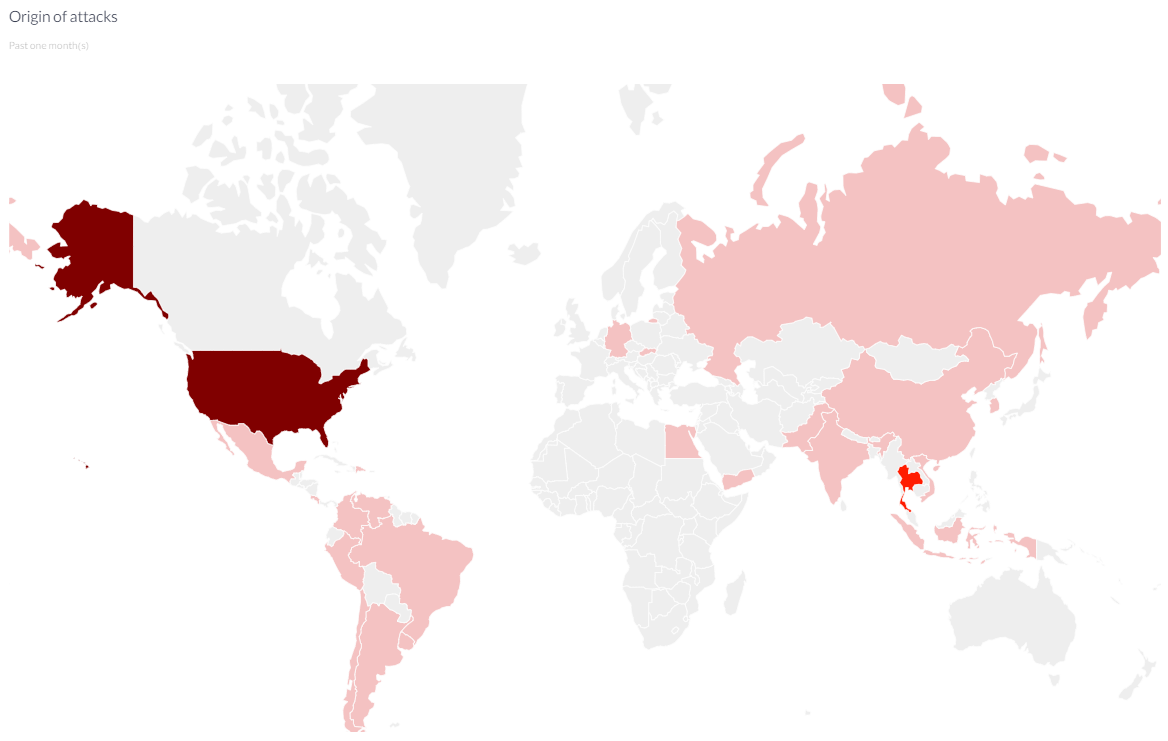
In the Origin of attacks section, you can see the areas that were attacked on your website.