Firewall Settings
The new generation of Arvancloud Firewall will provide you with a flexible space to control your website or application’s HTTP requests. Our firewall settings help you create rules by combining several conditions to control domain traffic and ensure the security of your website and web application.
Arvancloud firewall makes it possible to examine and block suspicious traffic by setting rules based on Wireshark. You can use your user panel or the CDN service’s API to apply these rules. This page helps you get started with these settings.
Arvancloud Firewall Activation and Configuration in User Panel
Go to the Firewall Settings under the CDN section of your account. Using the options in the "Default rule" section, you can make your website available in general by activating the allow option or disabling it by selecting the deny mode. The default rule will take action when the request’s condition does not match any other defined rules.
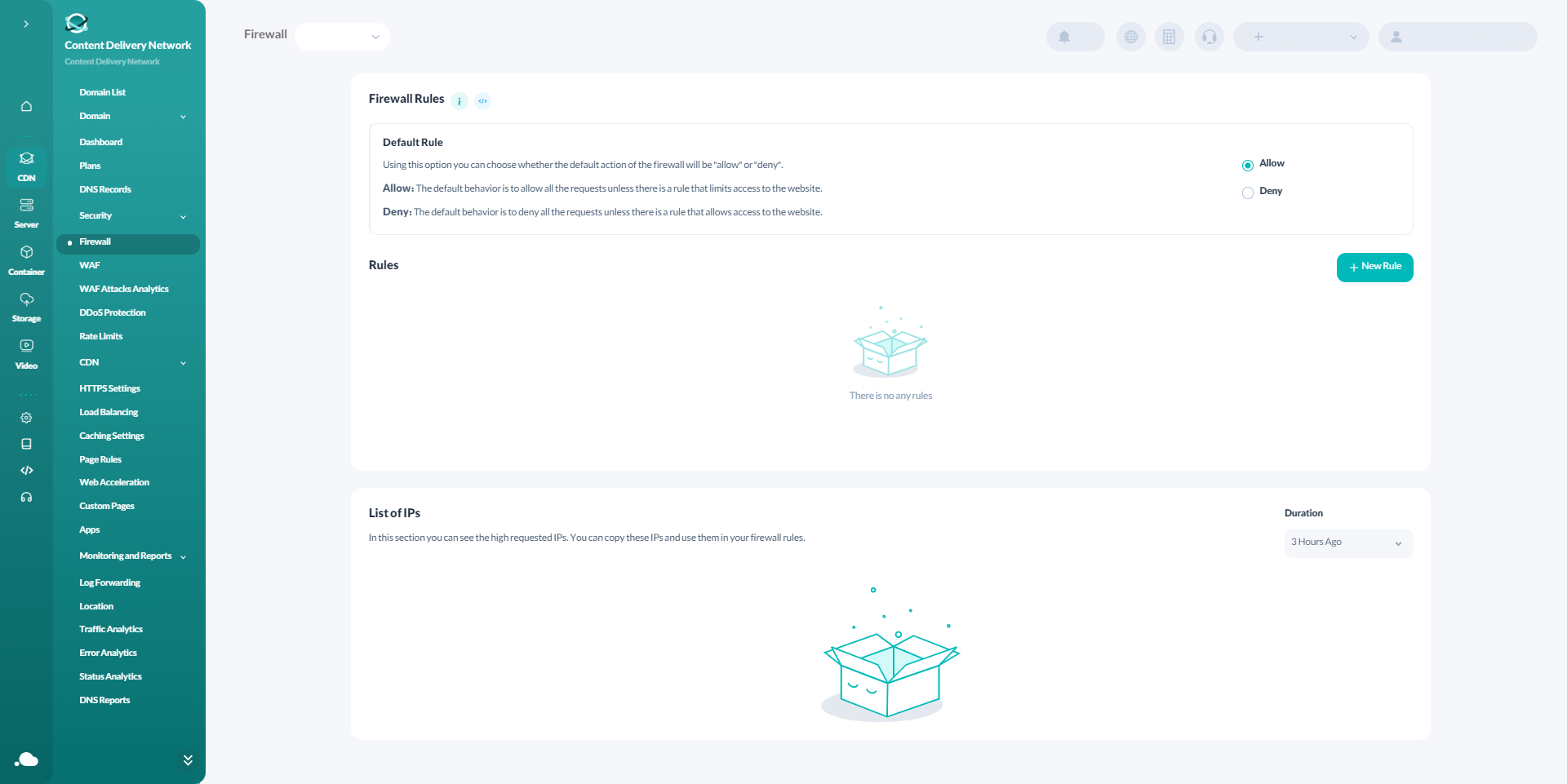
To define rules, you need to click on New Rule. You will be able to specify the name and description of the rule, parameter, operator and value of the condition, as well as check the equivalent expression of the rule. In the end, you can choose the action of whether to allow or deny after setting the conditions.
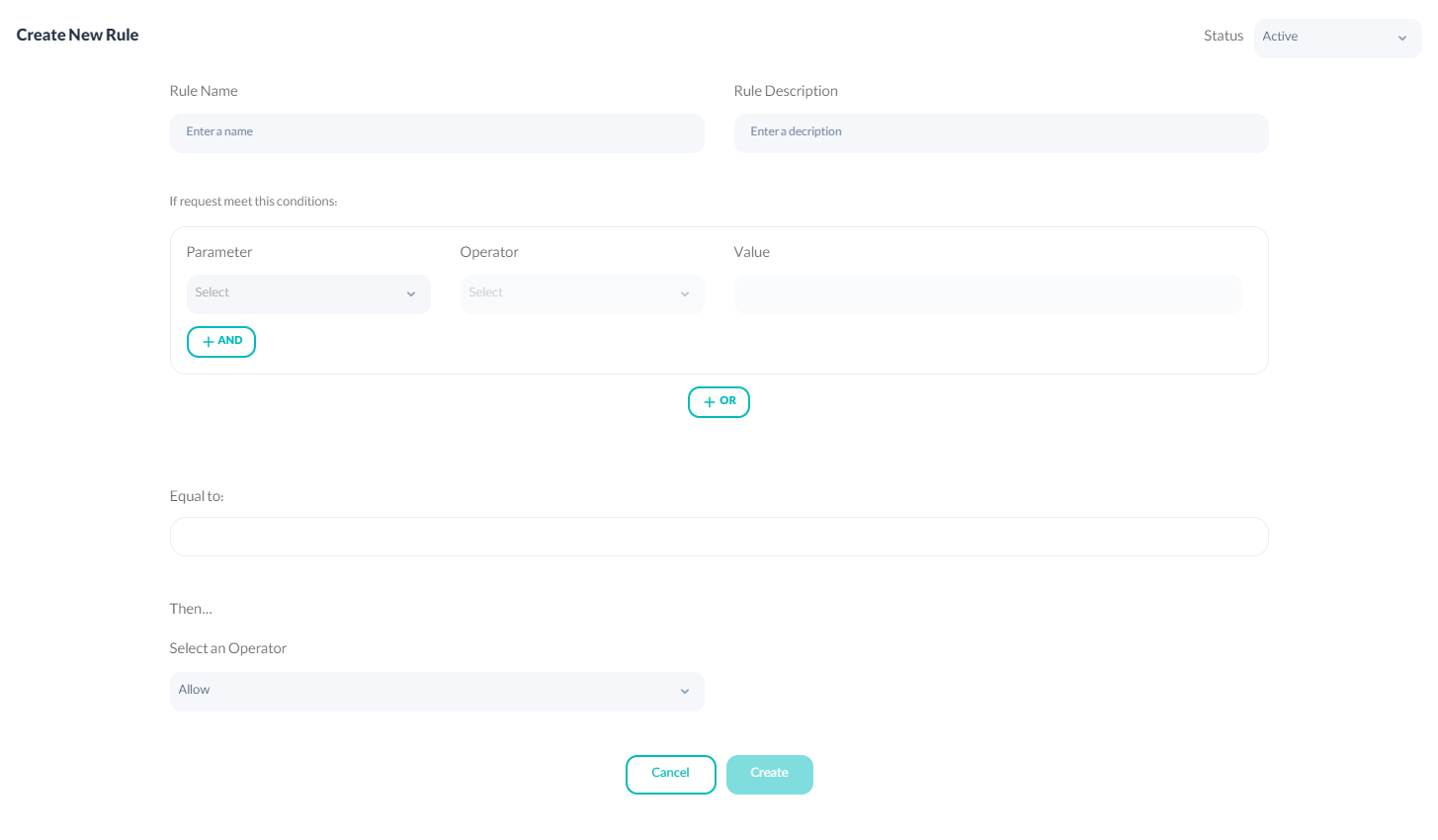
To set a condition, you need to fill the Parameter bar with your specific HTTP variable.
| Parameter | Description |
|---|---|
| SOURCE IP ADDRESS | Indicates the requester's IP Sample value: 1.2.3.4 |
| COUNTRY | Indicates the requester's country of origin Sample value: DE |
| URI PATH | Indicates the request uri path Example value: /help/index |
| HOSTNAME | Indicates the hostname used in the request Example value: www.example.com |
| COOKIE | Indicates the full value of the cookie as a character string Example value: SSID=AjMisfbW7_GcDfpgd;session=8521F670545D7865F79C3D7BEDC29CCE |
| REFERER | Indicates the HTTP Referer header of the request, which contains the address of the page linked to the currently requested page. Example value: developer.example.com/docs/Web/JavaScript |
| REQUEST METHOD | Indicates the HTTP request method in the form of a character string of uppercase letters Sample value: GET |
| URI | Indicates the querystring and the uri path Sample value: /help/index?section=539061&expand=comments |
| URI QUERY STRING | Indicates the full value of the querystring without the ? Sample value: section=539061&expand=comments |
| HTTP VERSION | Indicates the HTTP protocol version used in the request Example value: HTTP/1.1 |
| USER AGENT | Indicates the user agent of the request, which contains a character string to identify the user's operating system and browser. Sample value: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/65.0.3325.181 Safari/537.36 |
| REQUEST HEADERS RAW | Represents HTTP request headers in the form of arrays with the HTTP headers key |
Example value: {"content-type": ["application/json"]} |
As of the moment, these parameters are entirely available in the Enterprise Plan, and the other parameters of IP Source Address, Country, Hostname, and URL are available in all plans.
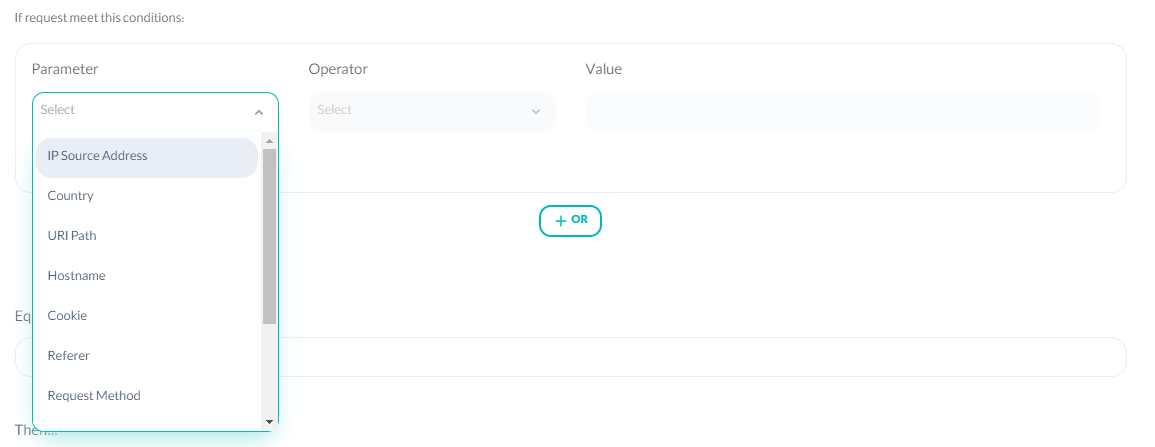
Next, you need to select the operator’s values from the table below and select a value to set a condition.
| Operator | Description |
|---|---|
| Equals | == shows the equal condition in the parameter and value |
| Not Equal | != and shows the not equal condition in the parameter and value |
| Contains | Contains and shows the condition having a value |
| Matches REGEX | ~ and shows the condition that the REGEX value is equal with the parameter |
| Is In a Set of | in and shows the condition has parameter values |
| Starts with | shows the starting condition of the parameter with a set value |
| Ends with | shows the ending condition of the parameter with a set value |
You have the option to set specific conditions in a rule to block or allow certain requests. If you add “and” between a number of conditions, it means that all the conditions must be matched, and if you add “or” between them, it means that if only one condition matches, the rule will work.
If you want to set a rule that all the incoming traffic of requests to a certain address using the POST method must be blocked, For example, to block example.com/test from one source IP and specific user-agent such as Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36, you need to follow this configuration:
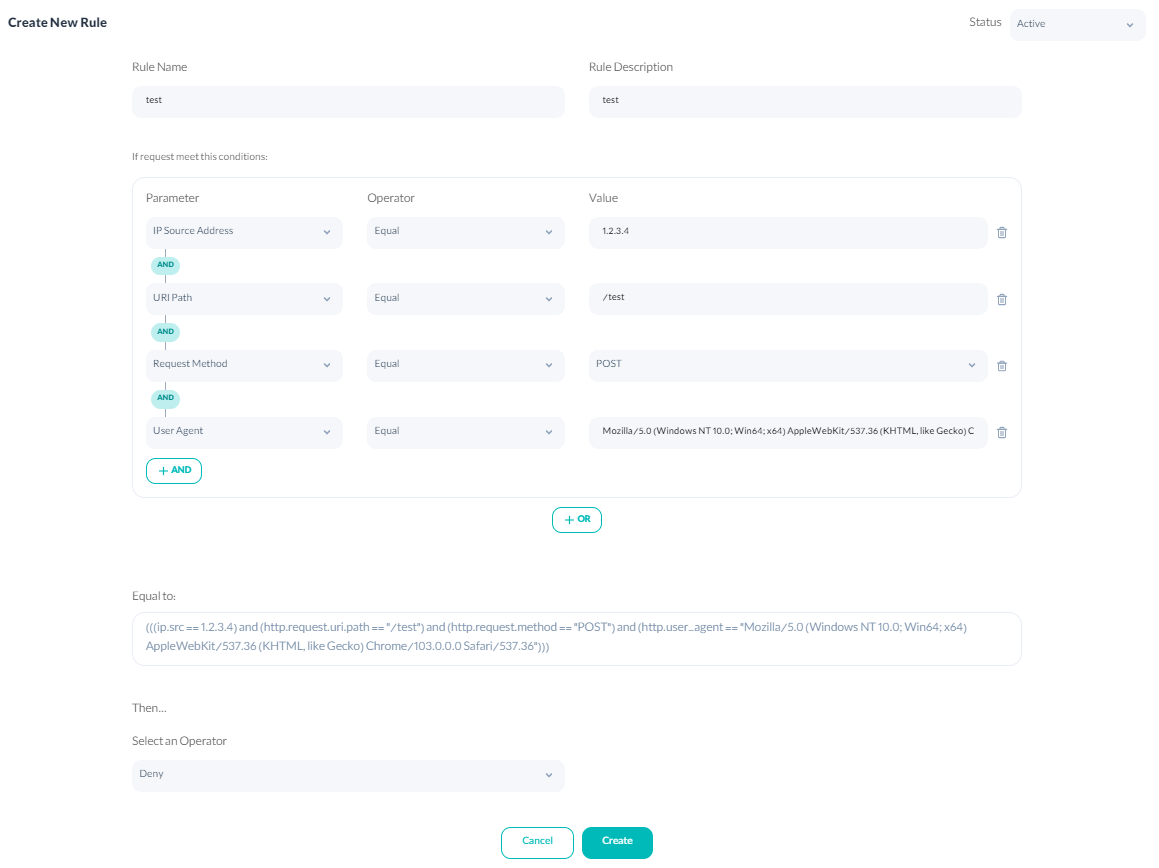
In the equal expression, you can examine the set condition and rule. A simple phrase will compare the HTTP request’s value with the defined value and will create a format of <value> <operator> <parameter> like ip.src==1.2.3.4. Complex expressions include simple expressions combined with and/or operators.
The phrase in the format of <simple phrase> <logical operator> <simple phrase> will be created, ((’ip.src==1.2.3.4)and(http.request.method==’POST)) Every firewall rule will have an equal expression according to the rules.
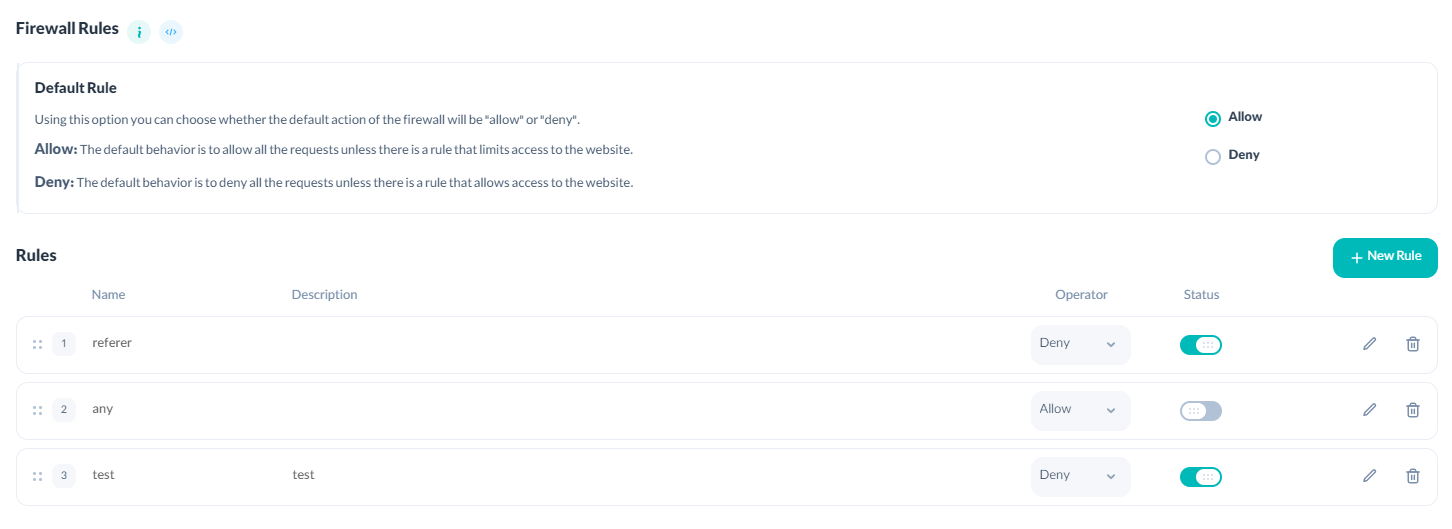
After defining and setting rules, you can edit, prioritize, and delete rules in the Rules list.
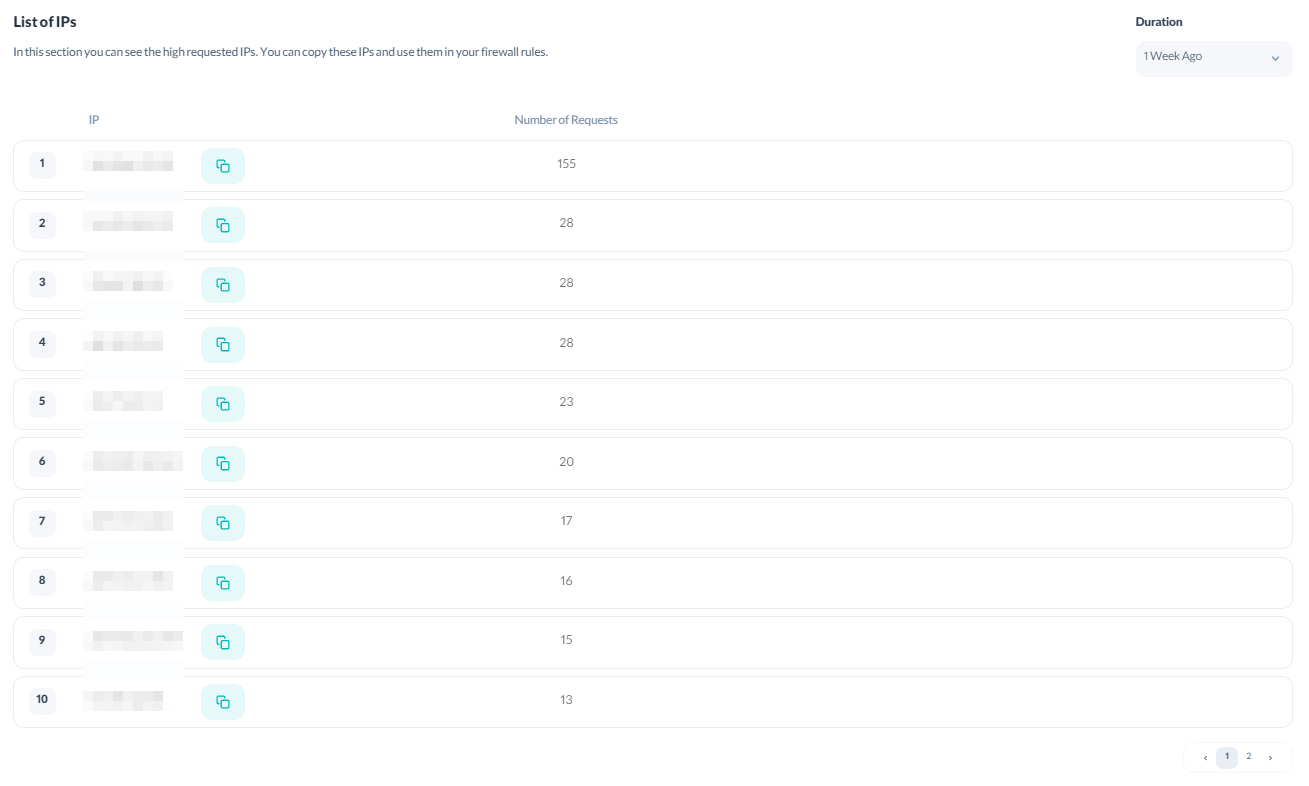
Furthermore, if you are on the Professional or Enterprise Plan, you can see the IP list of the visitors and access the number of their requests in the Firewall Settings.
Name, Description and Status of Rules
Each rule in the Arvancloud CDN firewall contains a name, description, and rule status.
For example, the user can assign a name to his rule and enter a description related to the function of the rule to identify and ease working with the rules. Finally, using the status field, it is possible to enable or disable the rule.

The name, description and state of rules' entries in the API can be defined using note, name and is_enabled parameters, where the is_enabled parameter has two values, true and false.
Firewall Behavior when a Condition Is Met
In Arvancloud's CDN Firewall, it is possible to determine what behavior the firewall will show if the conditions entered in a rule occur. Allow, block, challenge and bypass security mechanisms are the operators you can choose for this.
Allow
In this case, Arvancloud responds to the sent request according to the defined conditions.

Create a rule with the authorized operator using the API:
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data-raw '{"name":"Test Rule","note":"","is_enabled":true,"action":"allow","action_details":{"mode":1,"ttl":120,"https_only":false},"filter_expr":"((http.host == \"example.com\"))"}'
Deny
In this case, Arvancloud does not allow the sent request to be processed and returns a 403 error.

Create a rule with the deny operator using the API:
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--header 'origin: https://panel.arvancloud.ir' \
--header 'pragma: no-cache' \
--data-raw '{"name":"deny rule","note":"","is_enabled":true,"action":"deny","action_details":{"mode":1,"ttl":120,"https_only":false},"filter_expr":"((http.host == \"example.com\"))"}'
Challenge
In this case, if one of the conditions is met, the user will face a DDoS challenge. It is also possible to determine what type of DDoS challenge it is and how long it will be valid for.

Create a rule with the challenge operator using the API:
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API kEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--header 'origin: https://panel.arvancloud.ir' \
--header 'pragma: no-cache' \
--data-raw '{"name":"challenge","note":"challenge","is_enabled":true,"action":"challenge","action_details":{"mode":1,"ttl":120,"https_only":false},"filter_expr":"((http.host == \"example.com\"))"}'
-
In creating a rule with the challenge operator through the API, the mode parameter can be equal to three values: 1, 2, or 3, where value 1 is a cookie challenge, 2 is a JS challenge, and 3 is a captcha challenge.
-
The "ttl" parameter indicates the time period that the DDoS challenge is valid, and the user will not be authenticated again until it expires.
Bypass
In this case, it is possible to specify which of the security mechanisms should not be implemented when the firewall conditions occur. These mechanisms include rate limit, web firewall (WAF) and DDoS attack protection.

Creating a rule with Bypass operator using API:
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--header 'origin: https://panel.arvancloud.ir' \
--header 'pragma: no-cache' \
--data-raw '{"name":"ByPass","note":"","is_enabled":true,"action":"bypass","action_details":{"waf":true,"rlimit":true,"challenge":true},"filter_expr":"((http.host == \"example.com\"))"}'
Arvancloud Firewall Activation and Configuration in API
All firewall settings and features of the Arvancloud CDN service can also be applied, edited, and examined through the APIs in the table below:
| API | Description |
|---|---|
| GET DOMAIN'S FIREWALL CONFIGURATION | Receive Default Firewall Settings |
| UPDATE DOMAIN'S FIREWALL CONFIGURATION | Edit Default Firewall Settings |
| CREATE NEW FIREWALL RULE | Create a New Firewall Rule |
| GET FIREWALL RULE INFORMATION | Receive Information about a Firewall Rule |
| UPDATE THE FIREWALL RULE | Edit a Firewall Rule |
| DELETE FIREWALL RULE | Delete a Firewall Rule |
| CHANGE PRIORITY OF FIREWALL RULES | Change the Priority of a Firewall Rule |
The previous example through the API would be as the following.
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'Authorization: Apikey XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX' \
--header 'Content-Type: application/json' \
--data-raw '{
"name": "test ",
"note": "rule test",
"is_enabled": true,
"action": "deny",
"filter_expr": "(((ip.src == 1.2.3.4) and (http.request.uri.path == \"/test\") and (http.request.method == \"POST\") and (http.user_agent == \"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36\")))"
}'
To write the parameter value filter_expr, write a phrase based on Wireshark rules. You can use the table below to specify the values.
| Parameter | Equivalent |
|---|---|
| SOURCE IP ADDRESS | ip.src |
| COUNTRY | ip.geoip.country |
| URI PATH | http.request.uri.path |
| HOSTNAME | http.host |
| COOKIE | http.cookie |
| REFERER | http.referer |
| REQUEST METHOD | http.request.method |
| URI | http.request.uri |
| URI QUERY STRING | http.request.uri.query |
| HTTP VERSION | http.request.version |
| USER AGENT | http.user_agent |
| REQUEST HEADERS RAW | http.request.headers.raw |
To read the API documents of this feature, you can check here.
Common Usage
Here, we review the common usages of Arvancloud CDN service’s firewall and the required settings.
-
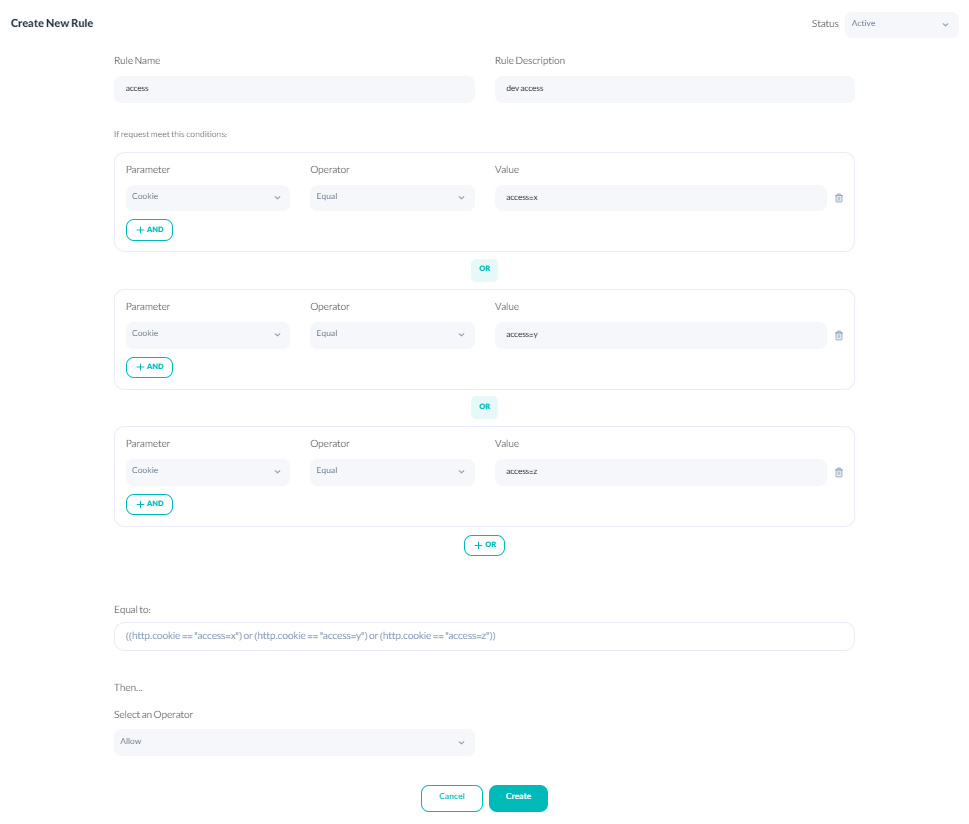
Requiring a Specific Cookie To secure an environment such as the developing one, you can share the cookie with trustworthy parties and filter the requests. This makes sure that the users who possess this cookie can access your specified address. For this purpose, you need to use the cookie parameter and set two rules. For example, you want to give access to only 3 of your colleagues to dev.example.com. First, you need to create a rule to block access to the address and allow access to certain users.
Please note that the allowing access rule must have a higher priority.
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'Authorization: Apikey XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX' \
--header 'Content-Type: application/json' \
--data-raw '{
"name": "acess",
"note": "dev access",
"is_enabled": true,
"action": "allow",
"filter_expr": "((http.cookie == \"acess=x\") or (http.cookie == \"acess=y\") or (http.cookie == \"acess=z\"))"
}'
-
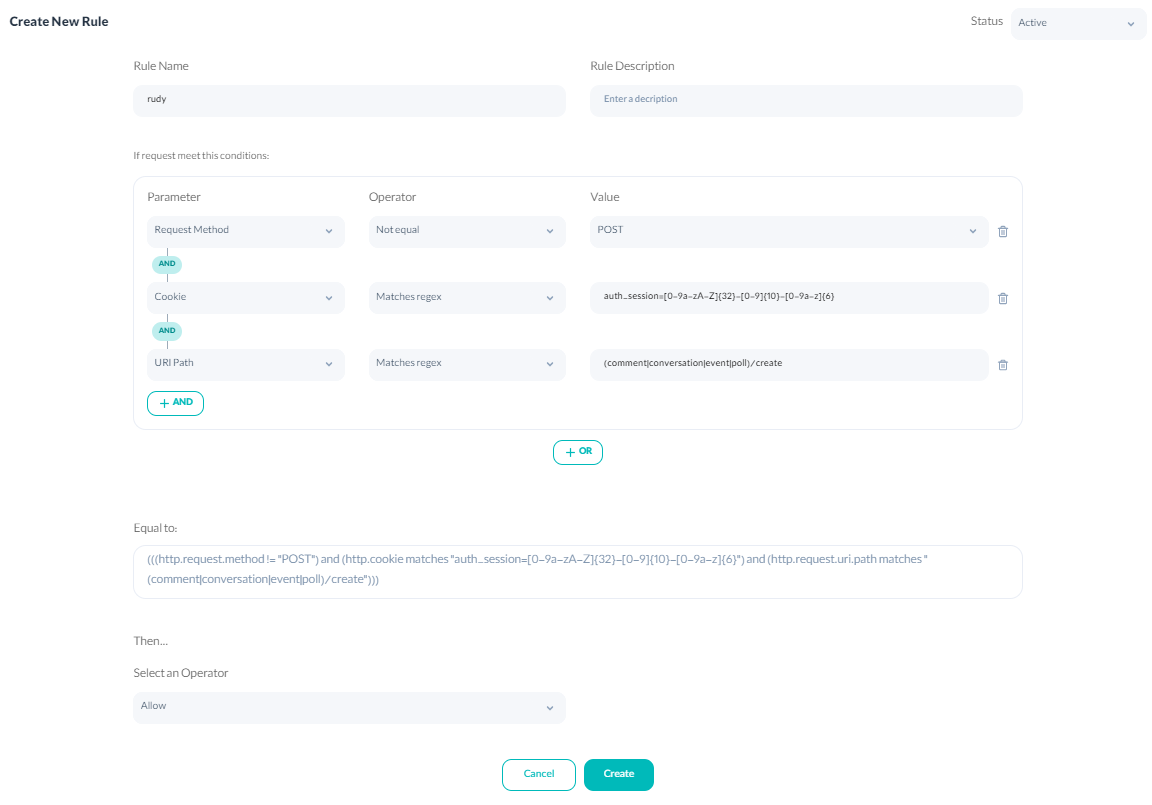
Protection Against R.U.D.Y These attacks are the DoS attacks that will send requests with bulky headers to loading sessions, and they cause the webserver to go out of service. To prevent these attacks, you need to block those requests that do not have the verified cookie. This example combines three conditions to block POST requests with incorrect cookies. The first parameter of the URI path condition specifies the addresses that need protection against R.U.D.Y:
((http.request.uri.path == "(comment|conversation|event|poll)/create"))
In the second condition, the format of the verified cookie is selected:
((http.cookie matches "auth_session=[0-9a-zA-Z]32-[0-9]10-[0-9a-z]6"))
The third condition distinguishes the requests other than the POST method:
((http.request.method != "POST"))
The three conditions are combined with “and,” and the rule’s performer is allowed.
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'Authorization: Apikey XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX' \
--header 'Content-Type: application/json' \
--data-raw '{
"name": "RUDY",
"note": "",
"is_enabled": true,
"action": "allow",
"filter_expr": "(((http.request.method != \"POST\") and (http.cookie matches \"auth_session=[0-9a-zA-Z]{32}-[0-9]{10}-[0-9a-z]{6}\") and (http.request.uri.path == \"\"(comment|conversation|event|poll)/create\")))"
}'
- Hotlink Prevention Hotlinking steals the website's bandwidth by providing direct links to the different parts of the website, such as images or videos. Using Arvancloud’s new generation of firewalls and setting specific rules can prevent hotlinking. You can protect the particular route using referrer and URI path parameters. As you can see in the image, in this rule, all requests from referrers other than the website example.com are blocked, and only those from this website are allowed.
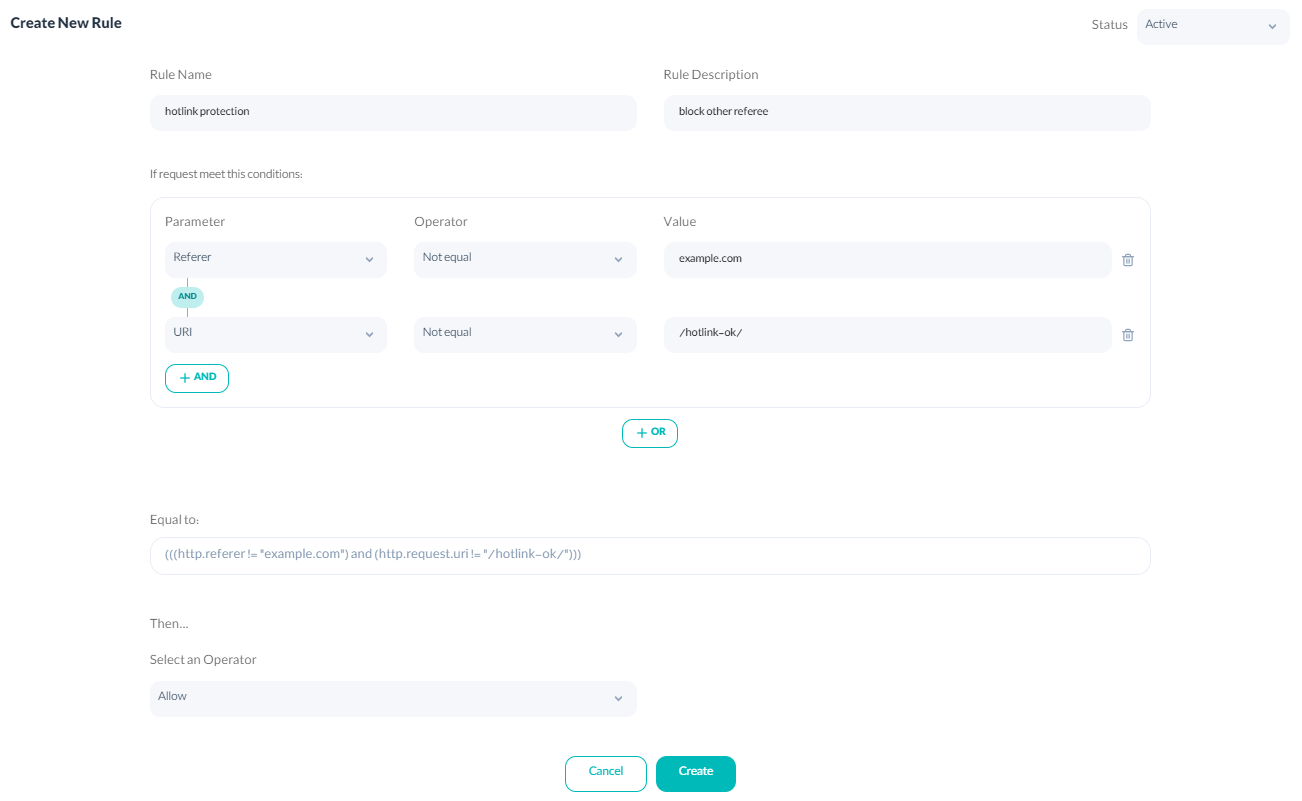
curl --location --request POST 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/firewall/rules' \
--header 'Authorization: Apikey XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX' \
--header 'Content-Type: application/json' \
--data-raw '{
"name": "Hotlink Protection",
"note": "block other referee",
"is_enabled": true,
"action": "deny",
"filter_expr": "(((http.referer != \"example.com\") and (http.request.uri != \"/hotlink-ok/\")))"
}'

