HTTPS Settings
You can manage the protocol connecting users with your website and the Arvancloud CDN service's edge servers in the Arvancloud account. You can also change the settings in the HTTPS protocol for content loading, settings for the free Arvancloud SSL/TLS certificate and upload your certificate. Other settings such as HSTS and HTTP2 can be accessed in this section.
HTTPS Activation
Activating this, the connection of your website users with CDN edge servers will be established on the HTTPS protocol, and the secure SSL/TLS protocol will be activated for your domain.
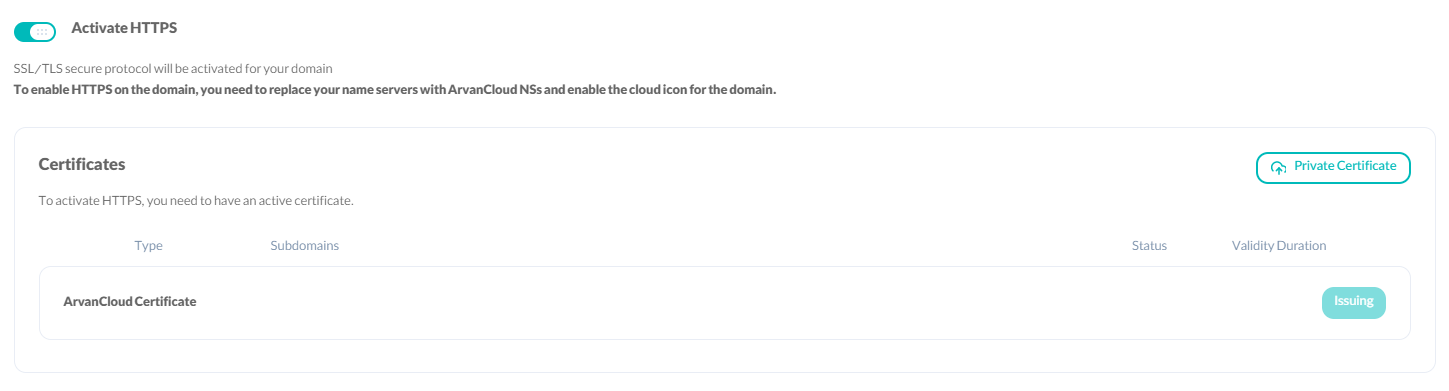
Activating the Arvancloud certificate gives you an SSL certificate through Let's Encrypt for your domain. This certificate is valid for 3 months and will be reactivated automatically.
Enabling HTTPS via API
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/ssl' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'content-type: application/json' \
--data '{"ssl_status":true}'
You can set the ssl_status key to false to disable this feature.
Custom SSL/TLS Certificate
You can also use your own SSL/TLS certificate by uploading a private certificate. By selecting this option and uploading the files related to the private key and certificate of your domain, in PEM format, your domain will use the uploaded private certificate.

Uploading Custom Certificate via API
curl --location 'https://napi.arvancloud.ir/cdn/4.0/domains/yourdomain.com/ssl/certificates' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'content-type: multipart/form-data; boundary=----WebKitFormBoundary7ZnkHJORO8lP1SVi' \
--data 'data'
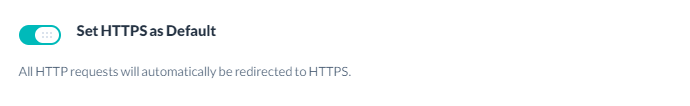
Setting HTTPS as Default
Activating this means that all of the HTTP traffic will be directed to HTTPS automatically. Using HSTS (HTTP Strict Transport Security) protocol, this is done in the safest possible way and will prevent possible Man-in-the-Middle attacks.
After activating and caching HSTS settings, it is impossible to apply changes until the configuration expires.
Enabling Default HTTPS via API
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/ssl' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data '{"https_redirect":true}'
You can set the https_redirect key to false to disable this feature.
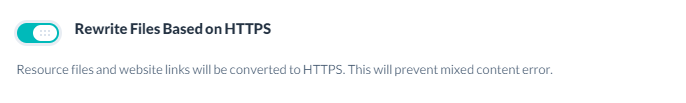
Rewriting Files Based on HTTPS
Activation of this option automatically changes all HTTP links in HTML and JS files with HTTPS ones.
Enabling HTTPS Rewriting via API
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/ssl' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'cache-control: no-cache' \
--header 'content-type: application/json' \
--data '{"replace_http":true}'
You can set the replace_http key to false to disable this feature.
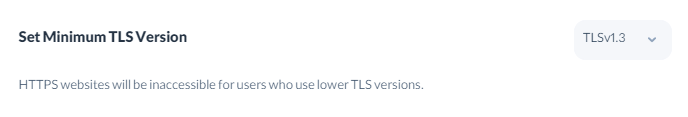
Configuring the Minimum TLS Version
In this section, you can select the minimum supported TLS version. When you choose the minimum TLS version, any user with an older TLS version cannot visit the website through HTTPS.
Setting TLS Version via API
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/ssl' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'content-type: application/json' \
--data '{"tls_version":"TLSv1.2"}'
In the tls_version key, put the value "" to set Default and "TLSvx.x" for other TLS versions.
HSTS Protocol
The main job of this protocol is to ensure the secure transfer of website links from HTTP to HTTPS. In the Arvancloud user panel, you can access all of its advanced settings, including the browser's required duration to display the webpage in HTTPS, the compatibility of all subdomains with HSTS, and preparing the domain for search engines.
Clicking on Edit Settings allows the activation of these features.
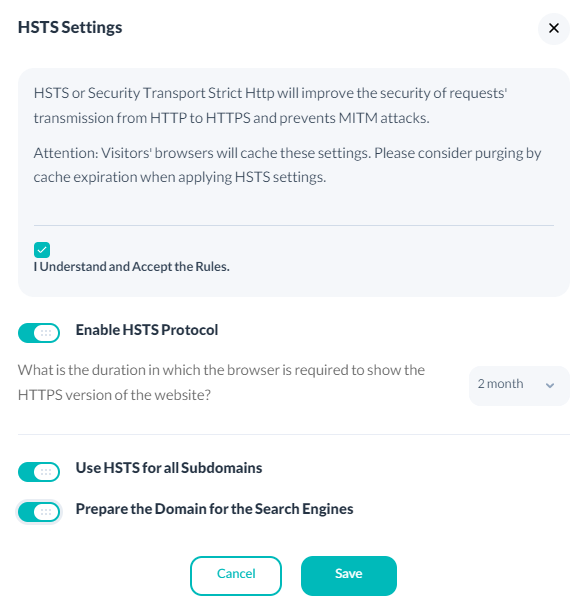
Most users connect to servers through HTTP protocol by default. If secure protocol becomes mandatory, these requests must automatically change to HTTPS. Using typical methods can have security risks. HSTS is a set of security policies that allow websites to be accessible only through the HTTPS protocol. These policies are announced to the user on a website by sending a header as Strict-Transport-Security.
Configuring HSTS via API
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/ssl' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'content-type: application/json' \
--data '{"hsts_status":true,"hsts_max_age":"2mo","hsts_subdomain":true,"hsts_preload":true}'
In this request, hsts_status, hsts_subdomain and hsts_preload keys accept true and false values. Also, to set the hsts_max_age key, the received parameter will be "xmo". (x is the duration, which can be one of the numbers 1-2-3-4-5-6-12 and 24)
Browser Reaction to HSTS
Receiving the user's request, the server sends a Header with HSTS protocol policies such as below:
Strict-Transport-Security: max-age=2628000; includeSubDomains;
This means that the domain and all subdomains will be only accessible through HTTPS for the next 2628000 seconds (1 month). The browser then does 2 important things:
- It changes all unsafe links to secure ones. For example, the website http://www.arvancloud.ir will become https://www.arvancloud.ir.
- If the browser cannot determine the website's security, it will display an error and will block access.
Google and Preload Solution
Suppose a user using a new operating system has entered a website address in the browser for the first time and in an unsafe environment. In this very first connection and receiving HSTS security policies, there is a security risk. In the Chromium project, Google decided to hardcode websites that needed to use HTTPS all the time. You can also add your website's name to this list by adding your domain to this page. Before, make sure your website matches these conditions:
- It has a valid certificate
- All HTTP traffic is transferred to HTTPS
- All subdomains are only accessible through HTTPS
- The correct header is sent to users for the configurations
Arvancloud does all of these items for you automatically. You only need to add your domain name to the Google list. Currently, Google Chrome, Firefox, Opera, Safari, and soon Microsoft Internet Explorer will use this Google list.
Browsers that Support HSTS
- Google Chrome version 4.0.211.0 and higher
- Firefox version 4 and higher
- Internet Explorer 11 and Microsoft Edge (Windows 10)
- Opera version 12 and higher
- Safari with OS X Mavericks since January 2013
Arvancloud's Default Connection Protocol with Main Servers
You can determine the connection method between your website's main servers and Arvancloud edge servers. The connection can be HTTP, HTTPS, or automatic. To enable the HTTPS or automatic option, your server needs to support the HTTPS protocol.
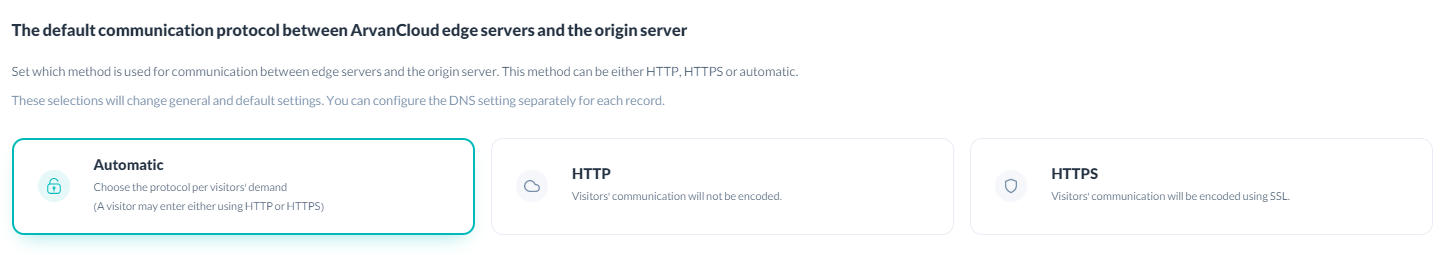
In the automatic setting, the protocols connecting the two groups of servers are determined by the users' requests. You can specify the connection protocol with the main server separately for each record in the activation section. If the protocol option is set to default in the activation section, the settings of this section will be applied.
Setting Connection Protocol via API
curl --location --request PATCH 'https://napi.arvancloud.ir/cdn/4.0/domains/example.com/load-balancers/settings' \
--header 'authority: napi.arvancloud.ir' \
--header 'accept: application/json, text/plain, */*' \
--header 'authorization: API KEY 1 2 3 4' \
--header 'Content-Type: text/plain' \
--data '{"protocol":"https"}'
The protocol key accepts http, https and auto.

